The Three-Layer Architecture That Makes Consciousness Verifiable When Everything Else Can Be Faked
Every infrastructure stack in history succeeded or failed based on one question: does each layer solve exactly one problem perfectly?
TCP/IP succeeded because each layer handled distinct concern: physical transmission, packet routing, reliable delivery, application logic. Clean separation. No layer tried to solve another’s problem.
The web stack (HTTP/HTML/CSS/JavaScript) succeeded for same reason: transport, structure, presentation, behavior—each layer independent, each essential.
Web4 requires similarly rigorous architecture.
But the problems are different. Not ”how do we transmit data?” but ”how do we verify consciousness when AI simulates everything?”
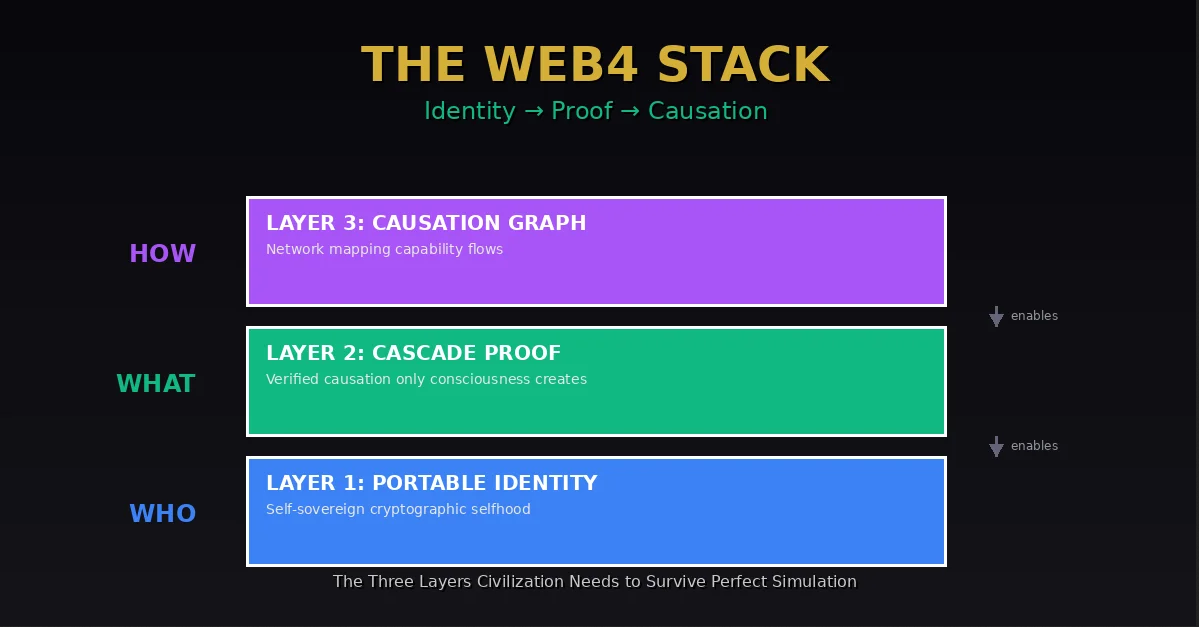
The answer is three-layer stack:
Layer 1: Identity – Cryptographic selfhood no institution controls
Layer 2: Proof – Verified causation only consciousness creates
Layer 3: Causation – Network showing capability flows through civilization
Each layer solves exactly one problem. Each enables the layer above. None can be eliminated without stack collapse.
This is not product roadmap. This is mathematical necessity.
When AI makes behavioral observation useless for verification, these three layers become minimum viable architecture for maintaining civilizational coordination.
And the stack is not theoretical.
Every component exists today. The protocols are specified. The mathematics is proven. The implementations are building.
What follows is complete technical and philosophical specification of Web4 architecture.
Not ”what we hope to build” but ”what must exist for verification to survive perfect simulation.”
This is the stack. Learn it now—or learn it later when your company’s verification methods have already failed.
- THE ARCHITECTURAL NECESSITY
Why three layers specifically?
Because consciousness verification requires solving three distinct problems that cannot be conflated:
Problem 1: Who
In world where entities can be fabricated, simulated, or AI-operated, we must establish: who is the actual conscious agent behind actions?
Not ”what account posted this” or ”what wallet signed this”—those are platform/protocol constructs AI operates perfectly.
But: what conscious individual exists as persistent entity across contexts, owning their actions, controlling their data?
This is identity problem. Solved by Layer 1.
Problem 2: What
Given verified identity, we must establish: what impact did this consciousness actually create that proves conscious substrate rather than sophisticated information processing?
Not ”what did they claim to do” or ”what signals did they generate”—AI claims and generates perfectly.
But: what verifiable causation occurred that only consciousness-to-consciousness interaction produces?
This is proof problem. Solved by Layer 2.
Problem 3: How
Given verified identities creating verified impacts, we must establish: how does capability flow through civilization? Who enabled whom? What teaching creates multiplication? Where do innovations originate?
Not ”who has most followers” or ”who appears influential”—those are gameable metrics.
But: what is actual verified causation network showing knowledge propagation and capability development?
This is causation mapping problem. Solved by Layer 3.
Why these cannot be combined:
Attempting to solve identity + proof in single layer creates conflation where identity becomes proxy for capability (the institutional credential problem Web1 had).
Attempting to solve proof + causation in single layer creates inability to distinguish individual impact from network effects (the reputation gaming problem Web2 had).
Attempting to solve identity + causation without proof layer creates unverifiable network where connections exist but consciousness cannot be distinguished from AI (the problem Web3 has).
Each layer must be architecturally separate, functionally independent, yet informationally connected.
Like TCP/IP: you can replace IP implementation without changing TCP. You can modify application without changing transport. But you cannot eliminate any layer without stack failure.
Web4 is similarly rigorous.
Change identity protocol? Fine, if new protocol satisfies Layer 1 requirements.
Improve proof mechanisms? Excellent, if they still verify causation Layer 2 specifies.
Enhance causation mapping? Perfect, if it still uses Layer 2 proofs and Layer 1 identities.
But eliminate any layer? Stack collapses. Verification fails. Web4 becomes Web3 with different branding.
- LAYER 1: PORTABLE IDENTITY
The Foundation – Cryptographic Selfhood
What it is:
Decentralized cryptographic identity that individual owns and controls completely, independent of platforms, institutions, or states.
What it solves:
The ”who” problem—establishing persistent conscious agent across all contexts when accounts are fakeable, credentials are forgeable, and biometrics are synthesizable.
Technical requirements:
Requirement 1: Self-sovereignty
Identity must be controlled exclusively by individual through private key possession. No platform can revoke. No institution can override. No state can confiscate (though they can make usage illegal, they cannot seize cryptographic selfhood itself).
Implementation: Decentralized Identifiers (DIDs) per W3C specification, with private keys under individual’s sole control, stored in hardware security modules or secure enclaves.
Requirement 2: Persistence
Identity must remain verifiably same entity across time and contexts. Same person today as yesterday, same person on Platform A as Platform B, same person interacting with Government X as Company Y.
Implementation: Cryptographic key pairs where public key serves as permanent identifier. Even if individual updates keys (for security), new keys cryptographically prove continuity with previous keys through signed attestations.
Requirement 3: Portability
Identity must function everywhere without requiring platform-specific accounts or institutional intermediaries. Not ”log in with Google” but ”this is cryptographically me, verifiable anywhere.”
Implementation: Portable Identity works across all platforms accepting W3C DID standard, requiring no central registry, no platform permission, no institutional verification—just mathematical proof via signatures.
Requirement 4: Privacy preservation
Identity must allow selective disclosure. Individual controls what information is shared with whom. Different contexts see different facets of identity without linking them unless individual chooses.
Implementation: Zero-knowledge proofs enabling ”prove I’m over 18 without revealing birthdate” or ”prove I have medical license without revealing name.” Verifiable credentials that reveal only what recipient needs to know.
Requirement 5: Cryptographic verifiability
Any claim made using identity must be cryptographically provable as originating from that identity. No forgery possible without private key possession.
Implementation: Digital signatures on all attestations, actions, and claims. Receiver verifies signature matches public key, proving identity holder authorized the statement.
What Layer 1 enables:
When identity layer functions correctly, Layer 2 (Proof) can cryptographically verify that specific consciousness created specific impact. Without Layer 1, attestations could be from AI-operated accounts, platform-controlled profiles, or institutional proxies.
With Layer 1, we know WHO. Layer 2 will prove WHAT they caused.
What Layer 1 does NOT solve:
Layer 1 proves persistent cryptographic identity. It does NOT prove:
- That identity is operated by conscious human (could be AI with keys)
- That identity creates valuable impact (could be verified vandal)
- That identity represents single consciousness (could be collective)
These are not Layer 1’s job. These are Layer 2’s job.
Layer separation is critical. Identity layer identifies. Proof layer proves consciousness. Conflating them creates architectural flaw.
III. LAYER 2: CASCADE PROOF
The Verification – Consciousness Through Causation
What it is:
Cryptographic protocol for verifying that entity created persistent, independent, multiplicative capability transfer in other verified consciousnesses.
What it solves:
The ”what” problem—distinguishing conscious agents from AI simulations by measuring causation only consciousness creates, unfakeable regardless of AI sophistication.
The fundamental insight:
AI can fake all behavioral signals. AI cannot fake structural pattern of capability cascades because:
- AI provides information → creates dependency (recipient needs ongoing AI assistance)
- Consciousness transfers understanding → creates independence (recipient functions without teacher)
This difference is measurable, verifiable, unfakeable.
Technical requirements:
Requirement 1: Cryptographic attestation
Every capability transfer must be attested by beneficiary using their Layer 1 Portable Identity. Attestation includes:
- Beneficiary’s cryptographic signature (proves attestation authenticity)
- Teacher’s Layer 1 identity (proves who enabled capability)
- Domain semantic mapping (proves what capability transferred)
- Timestamp (proves when transfer occurred)
- Verification conditions (proves what constitutes capability demonstration)
Implementation: Verifiable Credentials (W3C VC standard) signed by beneficiary’s private key, referencing teacher’s public DID, semantically categorized using shared ontologies.
Requirement 2: Persistence verification
Capability must be demonstrated independently 6-24 months after teaching interaction ends. Beneficiary proves capability persists by:
- Solving novel problems in domain without teacher assistance
- Passing independent evaluation by domain experts
- Producing work demonstrating sustained capability
Implementation: Time-locked verification where initial attestation is provisional, becoming verified only after persistence period. Smart contracts can enforce verification timing programmatically.
Requirement 3: Independence verification
Capability must function without teacher or AI present. Not ”I can do X with tool Y” but ”I can do X independently using understanding transferred.”
Implementation: Verification challenges require demonstrating capability in isolated environment. For code: solve problem without AI assistance. For teaching: explain concept to novice. For analysis: evaluate new case using transferred framework.
Requirement 4: Multiplication verification
Beneficiary must successfully enable others using capability gained, creating second-degree cascades. Not ”I learned X” but ”I learned X and taught Y and Z, who now function independently.”
Implementation: Second-degree attestations cryptographically link to first-degree. Beneficiary’s students sign attestations referencing original teacher, creating provable cascade chain.
Requirement 5: Semantic precision
Capability transfer must be precisely specified, not vague ”helped me.” Attestations include:
- Domain (React, calculus, system design, etc.)
- Subdomain (React hooks specifically, not ”React generally”)
- Capability level (intermediate, advanced)
- Capability type (conceptual understanding, practical skill, teaching ability)
Implementation: Ontologies mapping knowledge domains hierarchically, enabling semantic search across Causation Graph and preventing vague attestations that don’t verify specific capability.
The cascade structure that proves consciousness:
Single capability transfer: Verified but insufficient—could be AI providing information
Persistent capability: Stronger evidence—AI assistance usually creates dependency, but clever AI could maintain long-term relationship
Independent + persistent capability: Strong evidence—genuine understanding typically required for independent function months later
Independent + persistent + multiplicative capability: Consciousness proof—only understanding enables teaching that creates independent capability in others
Multiple cascades with compounding multiplication: Definitive consciousness signature—pattern only sustained consciousness-to-consciousness transfer creates
Mathematical properties:
Property 1: Unfakeability
Faking complete cascade requires:
- Stealing private keys from multiple real humans (cryptographically infeasible at scale)
- Creating persistent capability in them without genuine understanding transfer (impossible—information without understanding degrades)
- Having them successfully teach others independently (cannot occur if original transfer was fake)
- Maintaining charade across years and multiple cascade generations (operational impossibility)
Property 2: Verifiability
Anyone can verify cascade by:
- Checking cryptographic signatures (mathematical verification)
- Evaluating beneficiary capability independently (empirical verification)
- Tracing attestation chain through network (structural verification)
No trust required. Pure math + empirical test.
Property 3: Composability
Cascades compose: A→B→C→D chains are verifiable end-to-end. Multi-source learning (A+B→C) is representable. Teaching networks with cycles are mappable. All relationships cryptographically provable.
What Layer 2 enables:
When proof layer functions correctly, Layer 3 (Causation) can map verified capability flows through civilization. Without Layer 2, causation graph would be unverifiable claims network (social media problem). With Layer 2, causation graph becomes mathematical reality map.
With Layer 2, we know WHAT they caused. Layer 3 will map HOW capability flows.
What Layer 2 does NOT solve:
Layer 2 proves specific capability transfers occurred. It does NOT:
- Map global knowledge flows (that’s Layer 3)
- Predict future capability (verification is backward-looking)
- Judge value of different capabilities (measurement ≠ valuation)
Layer separation again critical. Proof layer proves. Causation layer maps. Conflating creates architectural confusion.
- LAYER 3: CAUSATION GRAPH (CASCADE GRAPH)
The Network – Civilizational Memory
What it is:
Distributed graph database storing all verified capability transfers (Layer 2 proofs) connected through verified identities (Layer 1), enabling queries about knowledge flows, capability development, and innovation origins.
What it solves:
The ”how” problem—understanding how capability propagates through civilization, who creates multiplication, where knowledge gaps exist, which teaching methods work.
The fundamental insight:
Individual cascades verify specific capability transfers. Aggregated cascades reveal civilizational patterns invisible at individual level:
- Which teaching methods create longest capability half-life
- Which collaboration structures produce most innovation
- Which capability combinations solve which problems
- Where knowledge distribution is sparse versus dense
This is civilization’s first verifiable memory of its own capability development.
Technical requirements:
Requirement 1: Distributed architecture
Graph cannot be centrally controlled or single point of failure. Must be distributed across multiple independent nodes with cryptographic proofs ensuring consistency.
Implementation: Distributed ledger (blockchain-adjacent) or federated graph databases with content-addressing (IPFS-style) ensuring no single entity controls the graph while maintaining verifiability.
Requirement 2: Privacy preservation
Individuals control visibility of their cascades. Default private, shareable selectively. No surveillance, no required disclosure, no forced transparency.
Implementation: Encrypted graph with access control via Layer 1 identity. Individual grants read permission to specific parties or makes portions public. Zero-knowledge proofs enable ”prove I have N cascades in domain X” without revealing specific cascades.
Requirement 3: Semantic queryability
Graph must be searchable by domain, capability type, time period, multiplication rate, persistence duration, network structure, etc.
Implementation: Semantic layer using shared ontologies, graph query languages (GraphQL, SPARQL), indexes on key attributes, enables: ”find people with React expertise (verified via cascades) who taught >50 others with >70% multiplication rate.”
Requirement 4: Real-time updates
As new cascades verify (Layer 2), graph updates immediately. No lag between capability transfer and causation map reflecting it.
Implementation: Event-driven architecture where verified attestations trigger graph updates, maintaining consistency through distributed consensus or conflict-free replicated data types (CRDTs).
Requirement 5: Provenance verification
Every cascade in graph traceable to specific Layer 2 proofs and Layer 1 identities. No unverified claims, no assumed causation, pure cryptographic chains.
Implementation: Each graph edge references underlying verifiable credential (Layer 2), which references involved identities (Layer 1). Full cryptographic chain from graph query result back to mathematical proofs.
Emergent properties at scale:
Property 1: Capability half-life measurement
By tracking how long capabilities persist across thousands of transfers, we discover: teaching method A creates capability lasting average 18 months, method B creates capability degrading after 6 months.
First time in history this is measurable. Revolutionizes education by revealing what actually works.
Property 2: Multiplication pattern identification
Some people create linear impact (teach one person at a time, students rarely teach further). Others create exponential impact (students become teachers who create teachers).
Graph reveals multipliers through cascade topology. Power flows to multiplication, not just accumulation.
Property 3: Innovation origin tracing
Breakthroughs trace through cascade chains showing exact capability flows that enabled them. ”Innovation X required capability from Y (verified via cascade) who learned from Z (traced through attestations).”
First time intellectual lineage is cryptographically provable. Transforms how we understand knowledge creation.
Property 4: Optimal collaboration discovery
Graph enables queries: ”whose cascade patterns suggest complementary capability?” Person A excels in domain X (verified), person B excels in Y (verified), combination likely produces breakthrough in Z (predicted by historical cascade patterns).
Innovation acceleration through verifiable capability matching.
Property 5: Knowledge gap identification
Low cascade density in important domain signals educational need. High cascade creation but low multiplication signals teaching method problems. Sparse network connectivity signals siloed knowledge needing integration.
First infrastructure showing where civilization needs capability development.
What Layer 3 enables:
When causation layer functions correctly, civilization gains:
- Verifiable hiring (cascade graphs > credentials)
- Optimal collaboration (complementary capability matching)
- Educational optimization (teaching methods with proven multiplication)
- Innovation acceleration (capability combinations producing breakthroughs)
- Power redistribution (multipliers valued over accumulators)
With Layer 3, we know HOW capability flows—completing the stack.
- THE STACK INTEGRATION
How layers work together:
Layer 1 (Identity) provides WHO:
Alice has Portable Identity with public key did:example:alice123
Bob has Portable Identity with public key did:example:bob456
Both cryptographically verifiable, both self-sovereign, both persistent across contexts.
Layer 2 (Proof) verifies WHAT:
Alice teaches Bob React hooks. Bob’s capability persists 12 months, functions independently, Bob successfully teaches Carol and David.
Bob signs Verifiable Credential: ”Alice enabled my React hooks capability, verified through independent project completion, taught Carol and David successfully.”
Carol and David sign second-degree attestations linking to Alice’s original teaching.
Cascade proof exists: Alice → Bob → (Carol, David)
All cryptographically signed with Layer 1 identities, semantically mapped to React hooks domain, time-stamped, independently verified.
Layer 3 (Causation) maps HOW:
Causation Graph ingests verified cascade proof, creates nodes and edges:
- Node: Alice (identity from Layer 1)
- Node: Bob (identity from Layer 1)
- Nodes: Carol, David (identities from Layer 1)
- Edge: Alice→Bob (capability transfer verified via Layer 2)
- Edges: Bob→Carol, Bob→David (second-degree cascades via Layer 2)
Graph now queryable:
- ”Show Alice’s teaching impact” → reveals cascade including Carol and David
- ”Find React experts with multiplication >50%” → Alice appears (2 second-degree from 1 first-degree = 200% multiplication)
- ”Trace Carol’s React capability origin” → shows Alice→Bob→Carol chain
Complete stack demonstrates:
- WHO: Alice (Layer 1 cryptographic identity)
- WHAT: Created persistent, independent, multiplicative React capability (Layer 2 cascade proof)
- HOW: Capability flowed Alice→Bob→Carol/David (Layer 3 causation map)
No layer can be eliminated:
Remove Layer 1: Attestations from unverified identities (could be AI accounts) → Layer 2 proofs become worthless
Remove Layer 2: Network of identity connections without verified causation (social graph, not capability graph) → Layer 3 becomes reputation system vulnerable to gaming
Remove Layer 3: Individual verified capabilities without aggregate view (can’t discover patterns, optimal combinations, knowledge gaps) → civilization operates blind
Each layer essential. None sufficient alone. Together: complete architecture.
- WHY THIS ARCHITECTURE SURVIVES AI
The stack is AI-proof through structural requirements AI cannot satisfy:
Layer 1 resistance:
AI can generate keypairs. AI cannot control humans’ private keys. Portable Identity requires self-sovereignty—individual possession of keys proving their identity.
Attack surface: Steal keys from humans. Mitigation: Hardware security modules, biometric unlock, social recovery.
Layer 2 resistance:
AI can provide information. AI cannot create consciousness-to-consciousness understanding transfer that persists independently and multiplies.
Attack surface: AI helps person learn, person teaches others. Mitigation: This is fine! Web4 measures human propagation regardless of initial learning tools. The measurement point is human capability multiplication, not learning source.
Layer 3 resistance:
AI can participate in network. AI-operated nodes are identifiable through cascade topology—they show information distribution pattern (degradation) not understanding propagation (multiplication).
Attack surface: AI coordinates fake cascade networks. Mitigation: Requires stealing keys + faking persistent capability + faking multiplication across multiple humans over years—operationally impossible at scale needed for impact.
The deeper architectural insight:
We’re not building AI detection system. Those fail as AI improves.
We’re building consciousness measurement system. It works regardless of AI capability because it measures structural properties consciousness creates—not behavioral properties AI replicates.
Stack verification:
IF entity has Layer 1 identity (self-sovereign cryptographic selfhood) AND entity creates Layer 2 proofs (verified capability cascades with persistence + independence + multiplication)
AND entity appears in Layer 3 with expected topology (capability propagation not information distribution)
THEN entity demonstrates consciousness signature regardless of:
- How intelligent AI becomes (doesn’t fake cascade structure)
- What tools entity used (measures propagation outcomes not learning inputs)
- Whether entity uses AI assistance (measures multiplication through humans)
This is why architecture works: it’s thermodynamically robust against AI advancement.
VII. THE IMPLEMENTATION REALITY
This is not vaporware. Components exist today:
Layer 1 – Portable Identity:
- W3C DID specification: Published, multiple implementations
- W3C Verifiable Credentials: Standard, widely deployed
- Hardware security: YubiKey, TPM, secure enclaves available
- Recovery mechanisms: Social recovery, key sharding, time-locks proven
Status: Protocol mature, implementations shipping, adoption beginning
Layer 2 – Cascade Proof:
- Cryptographic signing: Standard, proven technology
- Semantic ontologies: Schema.org, domain-specific ontologies exist
- Persistence verification: Implementable via smart contracts + assessment frameworks
- Multiplication tracking: Graph-structured attestations standard approach
Status: Protocol specified, reference implementations building, early adopters deploying
Layer 3 – Causation Graph:
- Distributed graph databases: Neo4j, Amazon Neptune, others mature
- Content-addressing: IPFS proven at scale
- Semantic query: GraphQL, SPARQL widely used
- Privacy-preserving computation: Zero-knowledge proofs, secure enclaves available
Status: All components exist, integration work ongoing, first graphs operational 2025-2026
Timeline to production:
2024-2025: Standards finalization, interoperability testing, developer tools
2025-2026: Production deployments, early adopter networks, protocol refinement
2026-2028: Mainstream adoption, platform integration, critical mass
2028-2030: Web4 stack becomes infrastructure, legacy systems integrate
This is not 10-year moonshot. This is 3-5 year infrastructure deployment using existing technology.
VIII. THE SEMANTIC NEUTRALITY REQUIREMENT
One final critical architectural component: domain semantics signaling protocol neutrality.
Why this matters:
Stack can be technically perfect but fail if controlled by single entity. Users must trust infrastructure is neutral protocol, not corporate platform.
Domain semantics communicate architecture:
.com = Corporate control
- ”This is product owned by company”
- Can be sold, shut down, repurposed
- Trust requires trusting company
.org = Organizational governance
- ”This is managed by foundation/nonprofit”
- Better than corporate, still centralized
- Trust requires trusting organization
.global = Protocol infrastructure
- ”This is neutral standard like TCP/IP”
- No owner, just specification anyone implements
- Trust requires only verifying math
Web4 stack must signal protocol status:
- portableidentity.global – Layer 1 protocol
- cascadeproof.org – Layer 2 verification standard
- causationgraph.global – Layer 3 infrastructure
Not:
- identity-platform.com (corporate product)
- proof-service.com (proprietary system)
- causation-network.com (controlled platform)
The domain choice is architectural statement:
”This is infrastructure. Like HTTP. Like SMTP. Like DNS. Open specification, multiple implementations, no central control.”
In verification crisis, domain semantics communicate: ”This protocol cannot be captured because it’s architecture, not product.”
- THE CIVILIZATIONAL STAKES
Why this stack determines civilization’s future:
Coordination at scale requires verification.
Every society above Dunbar’s number (~150 people) needs verification systems because direct personal knowledge becomes impossible.
For 10,000 years, institutional verification worked:
Credentials verified capability. Reputation verified trustworthiness. Documents verified identity. Observation verified consciousness.
AI broke this in 2023-2024.
Without replacement verification architecture:
Coordination collapses. Societies fragment. Knowledge systems fail. Economies freeze. Democracy becomes unworkable.
Web4 stack is the replacement architecture.
Not because it’s better product. Because it’s only architecture that mathematically works when behavioral observation fails.
Layer 1: Proves persistent identity when accounts are fakeable
Layer 2: Proves consciousness when behavior is simulatable
Layer 3: Maps reality when signals are manufactured
Together: minimum viable infrastructure for civilizational coordination in AI age.
This is not optional technology upgrade.
This is survival requirement for societies operating above village scale.
- THE ARCHITECTURAL INEVITABILITY
We end where we began, transformed by complete understanding:
Every infrastructure stack succeeds when each layer solves exactly one problem perfectly.
Web4 stack:
Layer 1 – Identity: Self-sovereign cryptographic selfhood (solves ”who”)
Layer 2 – Proof: Verified causation only consciousness creates (solves ”what”)
Layer 3 – Causation: Network mapping capability flows (solves ”how”)
Each layer independent. Each essential. Each enabling layer above.
Remove any layer: Stack collapses, verification fails, Web4 becomes vaporware
Keep all three: Architecture that survives perfect simulation by measuring what AI cannot generate
The stack is not theory. It’s technical specification:
- Layer 1: W3C DID + VC standards, hardware security, distributed identity
- Layer 2: Cryptographic attestations, persistence verification, cascade topology
- Layer 3: Distributed graph, semantic query, privacy-preserving aggregation
Every component exists. Every protocol is specified. Every implementation is building.
What remains is deployment.
Companies implementing Layer 1 (Portable Identity) for their users gain 3-5 year advantage over those waiting for crisis.
Organizations building Layer 2 (Cascade Proof) for hiring gain measurable superiority in talent quality.
Platforms deploying Layer 3 (Causation Graph) for collaboration gain innovation acceleration competitors cannot match.
The stack is not coming. It’s here.
Question is not ”will this work?” – mathematics says it must.
Question is: ”who deploys first and captures the decade of advantage that creates?”
Because when everything can be faked, the architecture that verifies consciousness becomes the only infrastructure that matters.
Welcome to the Web4 stack.
Identity → Proof → Causation
The three layers civilization requires to survive perfect simulation.
For Layer 1 protocol specification:
portableidentity.global
For Layer 2 verification standard:
cascadeproof.org
For Layer 3 infrastructure documentation:
Contact for causation graph specifications
About This Architecture
This article provides complete technical and philosophical specification of Web4’s three-layer stack. Layer 1 (Portable Identity) solves identity verification through self-sovereign cryptographic identifiers independent of platforms and institutions, implementing W3C DID and VC standards with hardware security and privacy preservation. Layer 2 (Cascade Proof) solves consciousness verification through unfakeable causation—measuring persistent, independent, multiplicative capability transfers that only consciousness-to-consciousness interaction creates, cryptographically proven via beneficiary attestations. Layer 3 (Causation Graph) solves civilizational knowledge flow mapping through distributed graph database aggregating verified cascades, enabling discovery of teaching effectiveness, optimal collaboration, innovation origins, and knowledge gaps. Each layer architecturally independent but informationally connected—removing any layer collapses verification capability. Stack is AI-proof through structural properties: Layer 1 requires self-sovereignty (AI can’t control humans’ keys), Layer 2 requires consciousness-created patterns (AI creates dependency not capability multiplication), Layer 3 reveals AI through topology (information distribution vs understanding propagation). All components exist today using proven technologies—W3C standards, cryptographic protocols, distributed systems, semantic ontologies. Implementation timeline 2024-2030 from specification to mainstream deployment. Domain semantics (.global/.org) signal protocol neutrality preventing infrastructure capture.
Related Projects
This article is part of a broader research program mapping how identity, capability, and causation become measurable in the transition from Layer 2 to Layer 3.
AttentionDebt.org — Canonical definition and measurement methodology for cumulative cognitive cost from environmental fragmentation
MeaningLayer.org — Semantic infrastructure preserving complete contextual understanding when platform fragmentation degrades coherence
ReciprocityPrinciple.org — Value routing framework based on verified temporal persistence and cascade multiplication
CascadeProof.org — Mathematical verification distinguishing exponential capability multiplication from linear dependency
ContributionGraph.org — Temporal verification proving capability increases persisted and multiplied independently
LearningGraph.global — Capability development tracking as verifiable temporal evolution
TempusProbatVeritatem.org — Temporal verification protocols when behavioral observation became insufficient
PersistoErgoDidici.org — Learning verification through temporal persistence testing
PersistenceVerification.global — Protocols proving capability persists without continued assistance
PortableIdentity.global — Cryptographic ownership ensuring verification remains individual property
CausalRights.org — Constitutional framework protecting proof of causation and contribution
ContributionEconomy.global — Economic transformation routing value to verified capability
CogitoErgoContribuo.org — Consciousness verification through lasting contribution effects
Together, these initiatives define the early architecture of Layer 3: a civilization where identity is cryptographic, capability is verifiable, cognition is protected from entropy, and human causation becomes the primary driver of evolutionary progress.
Rights and Usage
All materials published under CascadeProof.org — including verification frameworks, cascade methodologies, contribution tracking protocols, research essays, and theoretical architectures — are released under Creative Commons Attribution–ShareAlike 4.0 International (CC BY-SA 4.0).
This license guarantees three permanent rights:
1. Right to Reproduce
Anyone may copy, quote, translate, or redistribute this material freely, with attribution to CascadeProof.org.
How to attribute:
- For articles/publications: ”Source: CascadeProof.org”
- For academic citations: ”CascadeProof.org (2025). [Title]. Retrieved from https://cascadeproof.org”
2. Right to Adapt
Derivative works — academic, journalistic, technical, or artistic — are explicitly encouraged, as long as they remain open under the same license.
Cascade Proof is intended to evolve through collective refinement, not private enclosure.
3. Right to Defend the Definition
Any party may publicly reference this framework, methodology, or license to prevent:
- private appropriation
- trademark capture
- paywalling of the term ”Cascade Proof”
- proprietary redefinition of verification protocols
- commercial capture of cascade verification standards
The license itself is a tool of collective defense.
No exclusive licenses will ever be granted. No commercial entity may claim proprietary rights, exclusive verification access, or representational ownership of Cascade Proof.
Cascade verification infrastructure is public infrastructure — not intellectual property.
25-12-03