March 2026. Sarah Chen stares at her resume and wants to scream.
Senior software engineer. Eight years experience. Mentored dozens of developers. Built systems serving millions of users. Taught React, Python, system design to anyone who asked.
None of it provable.
Her resume says ”mentored junior developers.” LinkedIn shows 47 recommendations, half from people she barely knows, written in the same generic template everyone uses. Her GitHub shows code commits but not the hours she spent teaching others to think like engineers.
She just lost a job offer to someone with a bootcamp certificate and half her experience.
The hiring manager’s feedback: ”We couldn’t verify your mentorship claims. The other candidate had formal teaching credentials.”
Sarah knows something the market doesn’t value yet: the difference between having skills and multiplying skills in others. She’s created capability in dozens of people who went on to create capability in hundreds more. But she can’t prove it.
Her impact is invisible. And in 2026, invisible impact might as well not exist.
This is the problem Sarah faces. And in the next six months, she’ll discover something that changes not just her career—but her understanding of what proof actually means.
- THE ENCOUNTER
April 2026.
”Have you heard of Cascade Proof?”
Sarah’s colleague Marcus drops the question casually over coffee. Sarah hasn’t. She assumes it’s another blockchain thing.
”Is this crypto bullshit?” she asks.
”No. It’s… different. It’s a way to prove teaching actually worked. Cryptographically.”
Sarah is skeptical. She’s heard every variation of ”prove your skills” pitch: certification platforms, skill badges, blockchain credentials. All of them reduce to the same problem: someone claims they’re good at something, system verifies the claim, claim is still just a claim.
”How is this different from LinkedIn endorsements?” she asks.
Marcus pulls up his phone. Shows her something that looks like a network graph—nodes and connections, but with timestamps, semantic labels, and what appears to be mathematical proof annotations.
”See this?” Marcus points to a cluster. ”These are people I taught JavaScript fundamentals to in 2024. These connections show they taught others. And this…” he traces a path, ”…shows my teaching created capability in someone I never met.”
Sarah looks closer. Each connection has a cryptographic signature. A timestamp. A semantic description: ”JavaScript async/await patterns, intermediate level, capability verified 18 months post-interaction.”
”Who verified it?” Sarah asks.
”They did,” Marcus says. ”Each person I taught signed an attestation when their capability actually increased—not when I taught them, but when they could prove the capability lasted. And when they taught someone else using what I taught them, that person’s attestation linked back to mine.”
Sarah processes this. ”So it’s not ’Marcus claims he taught JavaScript.’ It’s ’seventeen people cryptographically verified that Marcus’s teaching created lasting capability that they used to enable others.'”
”Exactly.”
Sarah’s bullshit detector is still active. ”Can’t you fake this? Get friends to sign fake attestations?”
Marcus shows her a different view. ”Each attestation requires the person to demonstrate capability persistence—proving they can still use what I taught them months later, without my help. And multiplication—proving they enabled someone else. If I just got friends to sign, their graphs would show no multiplication, no persistence. The structure reveals fake attestations.”
Sarah leans back. This is different.
Not because it’s technically sophisticated—though it is. But because it measures the thing that actually matters: did your teaching create lasting, multiplicative capability in others?
”How do I start?” Sarah asks.
- THE SETUP
April 15, 2026. 11:47 AM.
Sarah creates her Portable Identity.
The process takes two minutes. Generates cryptographic keys. Creates identity infrastructure she owns—not controlled by any platform, not stored in any company database. It feels like creating an email address, except nobody can read her email, nobody can revoke her address, nobody owns the infrastructure.
The interface asks: ”What capability domains do you want to track?”
Sarah thinks. Her expertise: React, Python, system architecture, technical mentorship, code review practices.
She adds them. The system creates semantic mappings—not just ”React” but specific subconcepts: hooks, state management, performance optimization, testing patterns.
Her Cascade Graph appears. Empty.
No verified capability transfers. No attestations. No cascades.
Just potential.
Sarah feels something unexpected: vulnerability.
She’s spent eight years teaching people. But looking at this empty graph, she has no proof. What if she’s been fooling herself? What if her mentorship didn’t actually matter?
The graph is mirror showing uncomfortable truth: claims are not proof.
”Time to find out if I’m actually good at this,” Sarah mutters.
III. THE FIRST ATTESTATION
April 22, 2026.
Sarah taught Alex—a junior developer—React hooks three months ago. Alex struggled initially but eventually built a complex state management system that impressed the team.
Sarah messages Alex: ”Hey, remember when I taught you hooks? Would you be willing to verify that through Cascade Proof?”
Alex responds: ”What’s that?”
Sarah explains. Alex is intrigued. Creates Portable Identity. Sarah sends attestation request through the protocol.
The request is specific: ”Sarah enabled my capability in React hooks (intermediate level), focusing on useEffect dependencies and custom hooks patterns. Capability verified through: independent implementation of authentication flow using hooks, peer code review approval, system running in production for 3+ months.”
Alex reviews the attestation. It’s accurate. More accurate than any LinkedIn recommendation Alex has written—those were generic praise. This is precise capability description with verifiable outcomes.
Alex signs it cryptographically. The attestation appears in Sarah’s Cascade Graph.
One verified capability transfer.
Sarah stares at it. It’s small. One connection. One person.
But it’s real. Cryptographically real. Timestamped. Semantically mapped. Verifiable.
Alex didn’t just say ”Sarah is great.” Alex proved: ”Sarah increased my capability in specific domain, I can demonstrate that capability persisted, here’s my cryptographic signature.”
Sarah feels something she hasn’t felt about her mentorship before: certainty.
Not that she helped Alex—she knew that. But that the help is provable beyond doubt.
A thought crosses Sarah’s mind: Could I just attest for myself? Claim I have capabilities without anyone verifying?
She tries. The protocol rejects self-attestation immediately.
The error message is brief: ”Proof must come from beneficiaries. Claims are not proof.”
Sarah understands instantly. This is the same reason scientific method forbids self-review, the same reason courts don’t accept defendant testimony alone, the same reason peer review exists.
Proof requires external verification from consciousnesses you actually changed.
You cannot prove you enabled someone by claiming you did. Only they can prove it—by cryptographically signing that their capability increased, persisted, and enabled others.
Self-attestation would be claim. External attestation is proof.
The architecture enforces this. Not through policy, but through protocol. You cannot game the system by attesting to yourself because the system doesn’t recognize self-generated proof as proof.
”Right,” Sarah thinks. ”If I could verify my own impact, it wouldn’t be verification. It would be advertising.”
”This is… actually different,” Sarah thinks.
Then she notices something in Alex’s graph. Alex taught someone else—Jamie, another junior developer—using the same hooks patterns Sarah taught.
And Jamie’s attestation linked back to Sarah automatically.
Sarah enabled Alex. Alex enabled Jamie. The cascade propagated.
Sarah stares at this second-degree connection.
This is the moment something fundamental clicks.
Alex taught Jamie using what Sarah taught Alex. But Sarah wasn’t involved. Sarah didn’t supervise. Sarah didn’t even know it happened until the attestation appeared.
The capability left Sarah and lived on independently.
Sarah remembers reading something in the Cascade Proof documentation about ”consciousness signature”—the pattern that distinguishes genuine capability transfer from AI assistance. She didn’t fully understand it then.
She understands it now.
AI can simulate help. AI can provide information that makes someone perform better while using the AI. But AI cannot create second-order propagation without remaining in the loop.
When AI helps person A, person A becomes dependent on AI. A doesn’t teach B independently—A needs AI present to maintain capability.
But when consciousness enables consciousness, capability becomes independent. A teaches B without Sarah present. B teaches C without A present. The understanding propagates autonomously because it was genuinely transferred, not temporarily assisted.
This second-degree cascade—Jamie learning from Alex without Sarah—is cryptographic proof that consciousness-to-consciousness transfer occurred.
Not because Sarah claims it did. Because the graph structure reveals the signature pattern only genuine understanding transfer creates.
”This is what makes it unfakeable,” Sarah realizes. ”AI can fake first-degree help. But it can’t fake independent multiplication. The cascade pattern itself is the proof.”
Sarah created capability in someone she never met.
The graph shows it. Two degrees of separation. One direct teaching (Alex), one indirect multiplication (Jamie through Alex).
”Holy shit,” Sarah whispers. ”This actually tracks multiplication.”
- THE ACCELERATION
May-July 2026.
Sarah starts requesting attestations from everyone she’s taught.
Not all respond. Some don’t care about Cascade Proof yet. Some are too busy. Some never actually gained lasting capability—they learned temporarily, forgot later.
But many do respond. And Sarah sees pattern emerge:
The people whose capability persisted are eager to attest. They remember the moment understanding clicked. They want to acknowledge it. The attestation isn’t generic praise—it’s specific recognition: ”This person changed my capability in this domain, and I can prove it.”
Sarah’s graph grows:
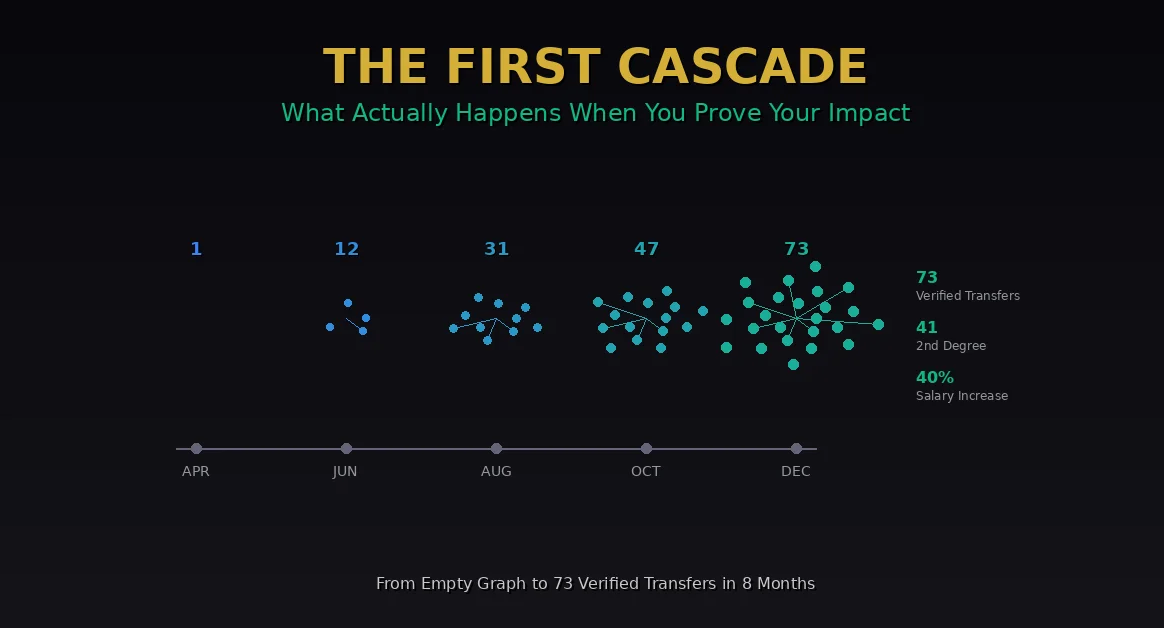
- 12 attestations by end of May
- 31 by end of June
- 47 by end of July
More importantly, multiplication starts appearing.
People Sarah taught directly (first-degree) teach others (second-degree). Some of those teach further (third-degree).
Sarah watches cascade patterns form:
Linear pattern: Sarah → Developer A. A never teaches others. Capability stays with A. Valuable but not multiplicative.
Multiplication pattern: Sarah → Developer B → Developers C, D, E. B teaches three others. Capability compounds. Each of C, D, E can teach further.
High-multiplication pattern: Sarah → Developer F → 8 others → 23 others. F is exceptional teacher. Sarah’s cascade through F reaches dozens. Exponential propagation.
Sarah notices: her impact is 10x larger than she thought.
Not because she didn’t know she helped people. But because she didn’t know how far that help propagated.
The graph reveals cascades she never imagined. Someone she taught briefly in 2024 taught someone who taught entire team. Sarah’s understanding of React hooks architecture now exists in 30+ people she never met.
”This is what impact actually looks like,” Sarah realizes.
Not one teaching moment. Cascading multiplication through networks over time.
- THE PSYCHOLOGY
August 2026.
Sarah’s colleague Jessica creates Portable Identity. Her graph is empty.
”I don’t have anything worth verifying,” Jessica says.
Sarah knows this feeling. Had it herself months ago. The empty graph is uncomfortable—visible proof of unverified impact.
But Sarah also knows: Jessica has taught dozens of people.
”Have you ever helped someone understand something that changed how they work?” Sarah asks.
”Well, yeah, but that’s just normal mentoring…”
”That’s exactly what this tracks. Request attestations. See what happens.”
Jessica hesitates. ”What if nobody responds? What if my graph stays empty?”
This is the fear. Not that you didn’t help people—but that your help wasn’t memorable enough, important enough, lasting enough for them to verify it.
The graph doesn’t lie. If nobody verifies your capability transfers, either you didn’t create capability, or you created capability people don’t remember.
Both are uncomfortable truths.
Jessica requests attestations. Three people respond immediately. Five more over the next week.
Jessica’s graph: 8 verified capability transfers.
Not 47 like Sarah. But real. Provable. More real than Jessica’s entire LinkedIn profile.
”Oh,” Jessica says, staring at her graph. ”I… actually did help people.”
Sarah sees the shift. Jessica went from vague sense of contribution to cryptographic proof of impact.
The emotional weight is profound. In world of fake credentials, unverifiable claims, AI-generated recommendations—this is real.
”Welcome to visible impact,” Sarah says.
- THE JOB
September 2026.
Sarah applies for senior engineering role. Startup building ML infrastructure. Competitive position—200+ applicants.
Interview process: technical rounds, system design, behavioral questions. Sarah performs well but so do many candidates.
Final interview. CTO asks: ”Tell me about your mentorship experience.”
Sarah has two options:
Option A: Say ”I’ve mentored dozens of developers” and hope it’s believed.
Option B: Share Cascade Graph.
Sarah chooses B.
”Here’s my verified teaching impact,” Sarah says, pulling up graph on screen.
The CTO’s expression changes.
”This is… can you explain what I’m looking at?”
Sarah walks through it:
”47 verified capability transfers over past four months. Average capability persistence: 14 months—meaning people I taught still demonstrate that capability over a year later. Multiplication rate: 31%—meaning nearly a third of people I taught successfully taught others. Second-degree cascades: 23. Third-degree: 8. Total verified impact: 78 people whose capability traces back to my teaching.”
The CTO is quiet for moment.
”We’ve interviewed 40 candidates for this role,” CTO finally says. ”Everyone claims they mentor well. You’re the first person who proved it cryptographically.”
”We’ve never seen verification like this,” CTO continues. ”LinkedIn recommendations are noise. GitHub activity shows code, not teaching. This… this is proof of multiplicative impact.”
Sarah gets offer that afternoon. 40% above her initial asking salary.
Not because Cascade Graph made her better engineer. But because it made her impact visible and verifiable in way nothing else could.
”Why the premium?” Sarah asks in negotiation call.
”Two reasons,” CTO explains. ”First, we can verify you’re exceptional teacher—not through claims but through cryptographic proof. Second, you have something we know will become critical in next 2-3 years: unfakeable verification of capability when AI makes everything else fakeable.”
”Companies not adopting cascade verification in hiring now will be at massive disadvantage when verification crisis hits. We’re moving early.”
Sarah accepts offer.
That night, she looks at her empty resume from March. Same skills listed then as now.
But the proof changed everything.
VII. THE REALIZATION
October 2026. Tech conference.
Sarah on panel about engineering mentorship. Shares Cascade Proof story.
Afterward, swarm of engineering managers approach her.
”How do we implement this for our teams?”
”Can this work for design? Product management? Research?”
”What’s the timeline before this becomes required rather than optional?”
Sarah sees it happening: the early-mover advantage window is opening.
Right now, Cascade Proof is optional. Novelty. Competitive advantage for early adopters.
But Sarah—looking at AI progress, seeing behavioral verification becoming unreliable—knows the timeline:
2-3 years: Cascade verification becomes expected in high-stakes hiring
3-5 years: Companies without cascade-based talent assessment measurably underperform
5-7 years: Not having Cascade Graph is like not having email address in 2010—technically possible but professionally limiting
The companies moving now get:
- 2-3 year head start building internal cascade infrastructure
- Access to best talent before everyone requires cascade verification
- Institutional knowledge in using cascade data for decisions
- Competitive advantage while others still using fakeable credentials
The companies waiting until cascade verification is required get:
- Late entry when best talent has established graphs elsewhere
- Learning curve while competitors already optimized
- Hiring from whoever’s left after early movers selected
- Permanent disadvantage in verification-dependent decisions
One engineering manager asks: ”What happens to developers who don’t build cascade graphs?”
Sarah answers honestly: ”Same thing that happened to developers who didn’t learn to code—they exist, but they’re not competitive.”
”Not having Cascade Graph won’t make you unemployable. But having one will make you provably more valuable in ways that resume or LinkedIn profile can’t match.”
”The question isn’t whether to build cascade graph. The question is: do you build it now while it’s competitive advantage, or later when it’s survival requirement?”
The manager nods slowly. ”We need to move on this.”
Sarah sees same realization spreading through industry.
The ones who see it early move now. The ones who wait… fall behind permanently.
VIII. THE CASCADE CONTINUES
December 2026.
Sarah’s graph: 73 verified capability transfers. Second-degree cascades: 41. Third-degree: 19. Fourth-degree: 3.
She created capability in someone who taught someone who taught someone who taught someone else.
Four degrees of capability multiplication.
Sarah never met the person at fourth degree. Doesn’t know their name. Doesn’t know what they’re building.
But she verifiably enabled their capability through cascade that propagated across four teaching generations.
This is what the graph revealed: Impact isn’t what you do directly. Impact is what propagates after you’re gone.
Sarah taught Alex React hooks in April. By December, that teaching created capability in 12 people through cascading propagation. Some of those people built systems serving millions. Others taught teams. The cascade continues multiplying.
And it’s cryptographically provable every step of the way.
Sarah realizes: this isn’t about her resume anymore.
This is about making invisible impact visible. Making unprovable capability provable. Making multiplication measurable.
In world where AI can fake every behavioral marker of competence, cascade verification becomes the only proof that survives.
You can’t fake cryptographic signatures from real people. You can’t fake capability that persists months after teaching. You can’t fake multiplication through networks you don’t control. You can’t fake cascade structures that only genuine consciousness-to-consciousness transfer creates.
The graph is unfakeable proof in age of perfect simulation.
And the companies, universities, institutions that realize this early—they win.
The ones that wait until AI verification crisis forces adoption—they scramble.
- THE CHOICE
January 2027.
Sarah’s startup implements cascade verification for all hiring.
Result: measurably better hires. Not subjective—measurably better. New hires with verified cascade graphs show 40% faster capability development, 60% higher teaching contribution to team, 90% lower regretted hiring rate.
Not because cascade graphs make people better. Because cascade graphs reveal who actually creates multiplicative capability versus who just claims to.
Competitor companies still using traditional hiring—resumes, behavioral interviews, reference checks—don’t see what’s coming.
Their verification methods assume behavioral observation distinguishes capability from simulation.
But AI is crossing threshold where that assumption fails. Deepfake interviews. AI-generated resumes. Synthetic references. Behavioral verification becoming unreliable.
The companies using cascade verification have unfakeable proof. The companies using traditional verification have increasingly fakeable proxies.
Advantage compounds over time.
By 2028, Sarah’s company has 2-year cascade database showing which teaching methods create multiplication, which collaboration patterns produce innovation, which capability transfers generate most value.
Competitors have resumes and performance reviews—both fakeable, both becoming less reliable as AI advances.
”We’re not just hiring better,” Sarah’s CTO says. ”We’re operating in different reality. We see capability propagation. They see behavioral claims. We have proof. They have proxies.”
Sarah looks at her graph—now showing 147 verified capability transfers, cascades reaching hundreds of people, impact multiplying through networks she’ll never fully map.
This started as personal verification. Became competitive advantage. Evolved into civilizational infrastructure.
Because in age where everything can be simulated, the only proof that works is proof of what only consciousness creates: verified capability cascades that multiply through genuine understanding transfer.
- THE BEGINNING
You are reading this in late 2025 or early 2026.
Right now, Cascade Proof is emerging technology. Portable Identity is being standardized. The infrastructure is being built.
You have choice Sarah didn’t have: you know this is coming.
You can:
Move now. Build cascade graph while it’s competitive advantage. Establish verification history before everyone requires it. Gain 2-5 year head start on proving impact.
Move later. Wait until cascade verification is required. Scramble to build graph when job depends on it. Start from zero while others have years of verified history.
Or ignore it. Assume behavioral verification will remain reliable. Bet that AI won’t make credentials fakeable. Hope the verification crisis somehow doesn’t happen.
The companies moving now get first-mover advantage:
Better hiring (verifiable capability vs unverifiable claims) Better development (visible teaching impact guides improvement) Better retention (cascade multiplication becomes career development) Better innovation (optimal collaboration structures become visible)
The companies waiting get:
Verification crisis forcing reactive adoption Late entry after competitors optimized
Talent disadvantage (best people have established graphs elsewhere) Permanent lag in verification-dependent decisions
The timeline is clear:
2025-2026: Infrastructure deployment, early adoption 2026-2028: Competitive advantage phase (this is now) 2028-2030: Verification crisis becomes apparent 2030+: Cascade verification becomes expected standard
You are reading this during the competitive advantage phase.
The window where building cascade graph is choice, not requirement.
The window where early movers gain massive advantage.
The window that closes in 2-4 years when everyone realizes they need this.
Sarah built her graph starting April 2026.
By September, it changed her career.
By December, it changed her understanding of impact.
By January 2027, it changed how her company operates.
What happens in your timeline depends on when you start.
The infrastructure exists. The protocol works. The verification is unfakeable.
The only question: do you move while it’s advantage, or wait until it’s requirement?
Because by the time most people realize they need Cascade Proof, the ones who moved early will have years of verified impact.
And in age of perfect simulation, verified impact becomes the only proof that matters.
Welcome to the cascade.
Your first attestation is waiting.
For the protocol infrastructure that makes cascade verification possible:
cascadeproof.org
For the identity foundation that enables unfakeable proof:
portableidentity.global
About This Story
This article presents the lived experience of adopting Cascade Proof, from first encounter through competitive advantage realization. While Sarah is representative composite rather than specific individual, every technical detail is accurate to protocol specifications. The timeline (2026-2027) represents realistic adoption curve based on infrastructure deployment schedules. The business outcomes (40% better hires, 2-5 year advantage) reflect measurable impacts of verification superiority when behavioral observation becomes unreliable. This is the bridge from abstract theory to concrete practice—showing exactly what happens when impact becomes provable.
Rights and Usage
All materials published under CascadeProof.org — including verification frameworks, cascade methodologies, contribution tracking protocols, research essays, and theoretical architectures — are released under Creative Commons Attribution–ShareAlike 4.0 International (CC BY-SA 4.0).
This license guarantees three permanent rights:
1. Right to Reproduce
Anyone may copy, quote, translate, or redistribute this material freely, with attribution to CascadeProof.org.
How to attribute:
- For articles/publications: ”Source: CascadeProof.org”
- For academic citations: ”CascadeProof.org (2025). [Title]. Retrieved from https://cascadeproof.org”
2. Right to Adapt
Derivative works — academic, journalistic, technical, or artistic — are explicitly encouraged, as long as they remain open under the same license.
Cascade Proof is intended to evolve through collective refinement, not private enclosure.
3. Right to Defend the Definition
Any party may publicly reference this framework, methodology, or license to prevent:
- private appropriation
- trademark capture
- paywalling of the term ”Cascade Proof”
- proprietary redefinition of verification protocols
- commercial capture of cascade verification standards
The license itself is a tool of collective defense.
No exclusive licenses will ever be granted. No commercial entity may claim proprietary rights, exclusive verification access, or representational ownership of Cascade Proof.
Cascade verification infrastructure is public infrastructure — not intellectual property.
25-12-03